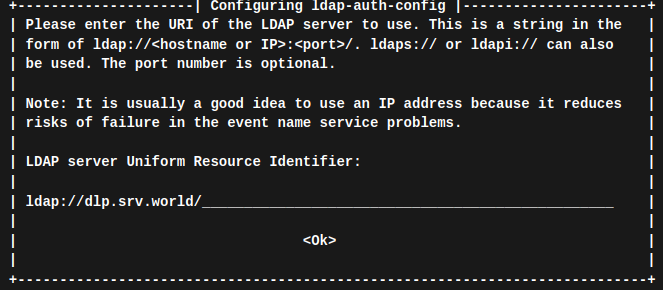
Als Basis dient OpenWrt 24.10.2 auf einem UniFi Security Gateway, der auch als DNS & DHCP Server arbeitet.
Packete die installiert werden müssen: libopenldap, openldap-server und openldap-utils.
Passwörter mit slappasswd erstellen:
slapd.conf anpassen:
# See slapd.conf(5) for details on configuration options.
# This file should NOT be world readable.
#
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
# Define global ACLs to disable default read access.
# Do not enable referrals until AFTER you have a working directory
# service AND an understanding of referrals.
#referral ldap://root.openldap.org
pidfile /var/run/slapd.pid
argsfile /var/run/slapd.args
# Load dynamic backend modules:
modulepath /usr/lib/openldap
moduleload back_mdb.la
# moduleload back_ldap.la
# Sample security restrictions
# Require integrity protection (prevent hijacking)
# Require 112-bit (3DES or better) encryption for updates
# Require 63-bit encryption for simple bind
# security ssf=1 update_ssf=112 simple_bind=64
# Sample access control policy:
# Root DSE: allow anyone to read it
# Subschema (sub)entry DSE: allow anyone to read it
# Other DSEs:
# Allow self write access
# Allow authenticated users read access
# Allow anonymous users to authenticate
# Directives needed to implement policy:
# access to dn.base=““ by * read
# access to dn.base=“cn=Subschema“ by * read
# access to *
# by self write
# by users read
# by anonymous auth
#
# if no access controls are present, the default policy
# allows anyone and everyone to read anything but restricts
# updates to rootdn. (e.g., „access to * by * read“)
#
# rootdn can always read and write EVERYTHING!
access to attrs=userPassword
by self write
by dn=“cn=Manager,dc=intern,dc=mynet,dc=net“ write
by anonymous auth
by * none
access to *
by self write
by dn=“cn=Manager,dc=intern,dc=mynet,dc=net“ write
by * read
#######################################################################
# config database definitions
#######################################################################
database config
# Uncomment the rootpw line to allow binding as the cn=config
# rootdn so that temporary modifications to the configuration can be made
# while slapd is running. They will not persist across a restart.
rootpw {SSHA}E/khaI0HYbBFnPS9ai/9iLfT1iozV3f8
#######################################################################
# MDB database definitions
#######################################################################
database mdb
maxsize 8388608
suffix „dc=intern,dc=mynet,dc=net“
rootdn „cn=Manager,dc=intern,dc=mynet,dc=net“
# Cleartext passwords, especially for the rootdn, should
# be avoid. See slappasswd(8) and slapd.conf(5) for details.
# Use of strong authentication encouraged.
rootpw {SSHA}E/khaI0HYbBFnPS9ai/9iLfT1iozV3f8
# The database directory MUST exist prior to running slapd AND
# should only be accessible by the slapd and slap tools.
# Mode 700 recommended.
directory /etc/openldap/openldap-data
# Indices to maintain
index objectClass eq
#######################################################################
# monitor database definitions
#######################################################################
database monitor
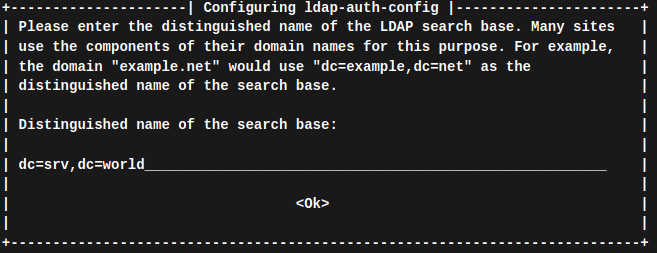
Domain Name und Gruppen anlegen:
lapadd -v -l /etc/openldap/ldif/base.ldif
dn: dc=intern,dc=mynet,dc=net
objectClass: top
objectClass: dcObject
objectClass: organization
dc: intern
o: Ournet
dn: ou=groups,dc=intern,dc=mynet,dc=net
objectClass: organizationalUnit
ou: groups
dn: ou=people,dc=intern,dc=mynet,dc=net
objectClass: organizationalUnit
ou: people
Benutzer anlegen:
lapadd -v -l /etc/openldap/ldif/user.ldif
dn: uid=john,ou=people,dc=intern,dc=mynet,dc=net
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
sn: Doe
givenName: John
cn: John
displayName: John Doe
uidNumber: 1001
gidNumber: 1001
userPassword: {SSHA}bOGwbbUNPstPiPT16PZZVL1Q1TmwsIQD
gecos: John Doe
loginShell: /bin/bash
homeDirectory: /home/john
dn: cn=john,ou=groups,dc=intern,dc=mynet,dc=net
objectClass: posixGroup
cn: john
gidNumber: 1001
memberUid: john
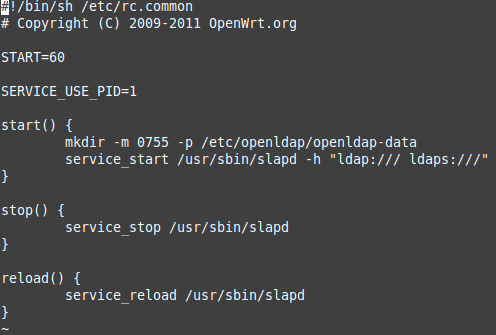
Startscript aufrufen „vi /etc/init.d/ldap“ und anpassen:
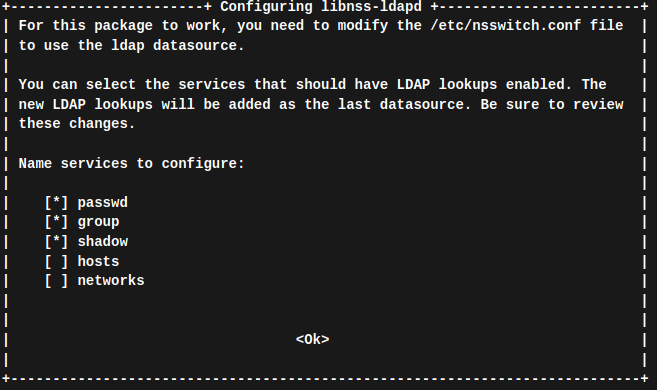
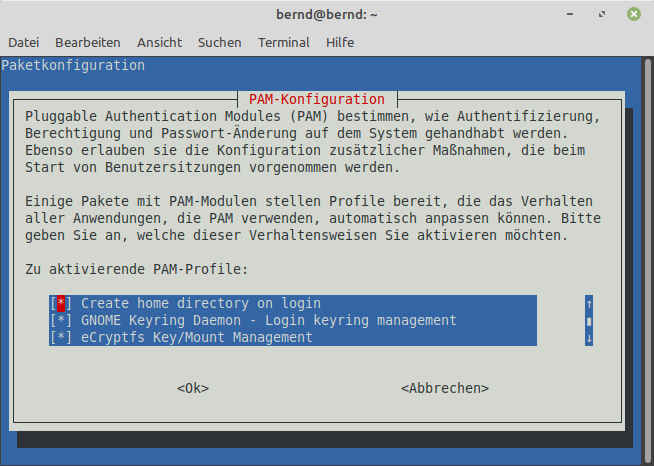
Client Linux Mint 21.3 vorbereiten: